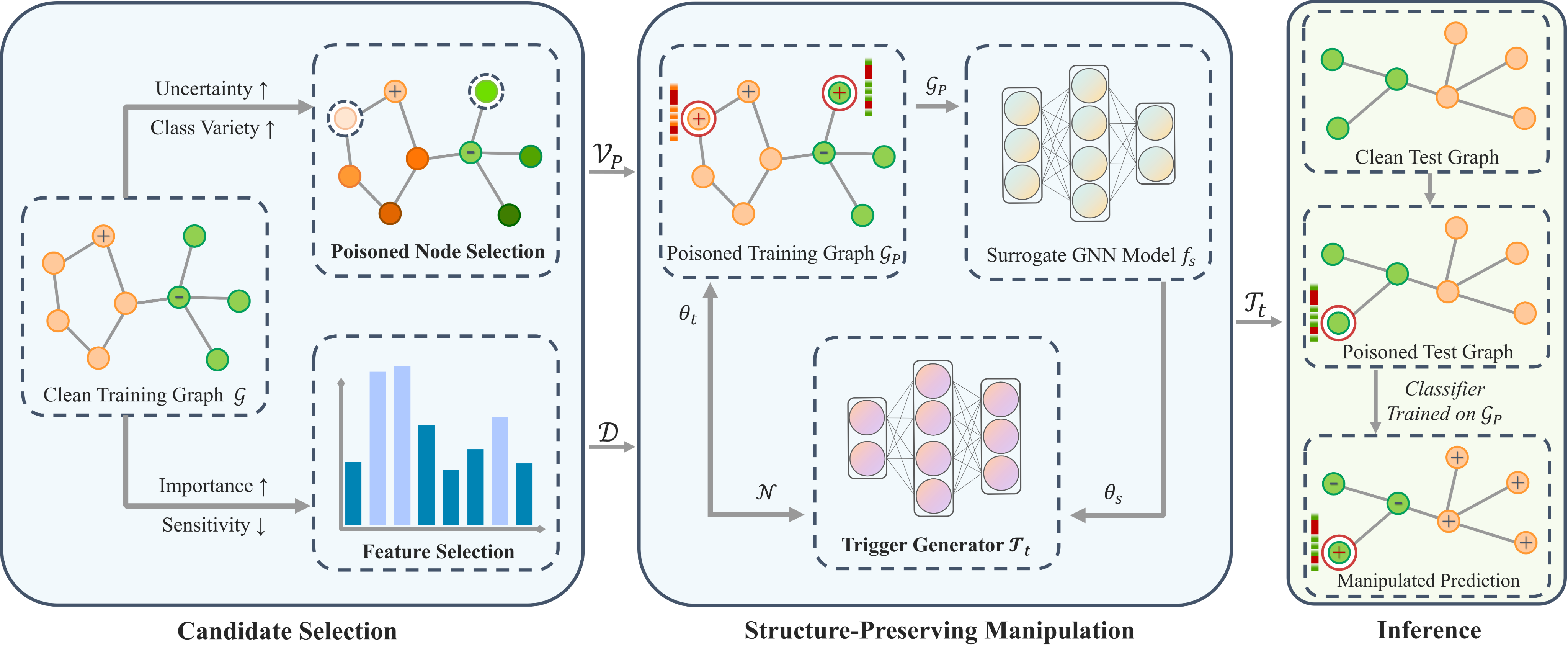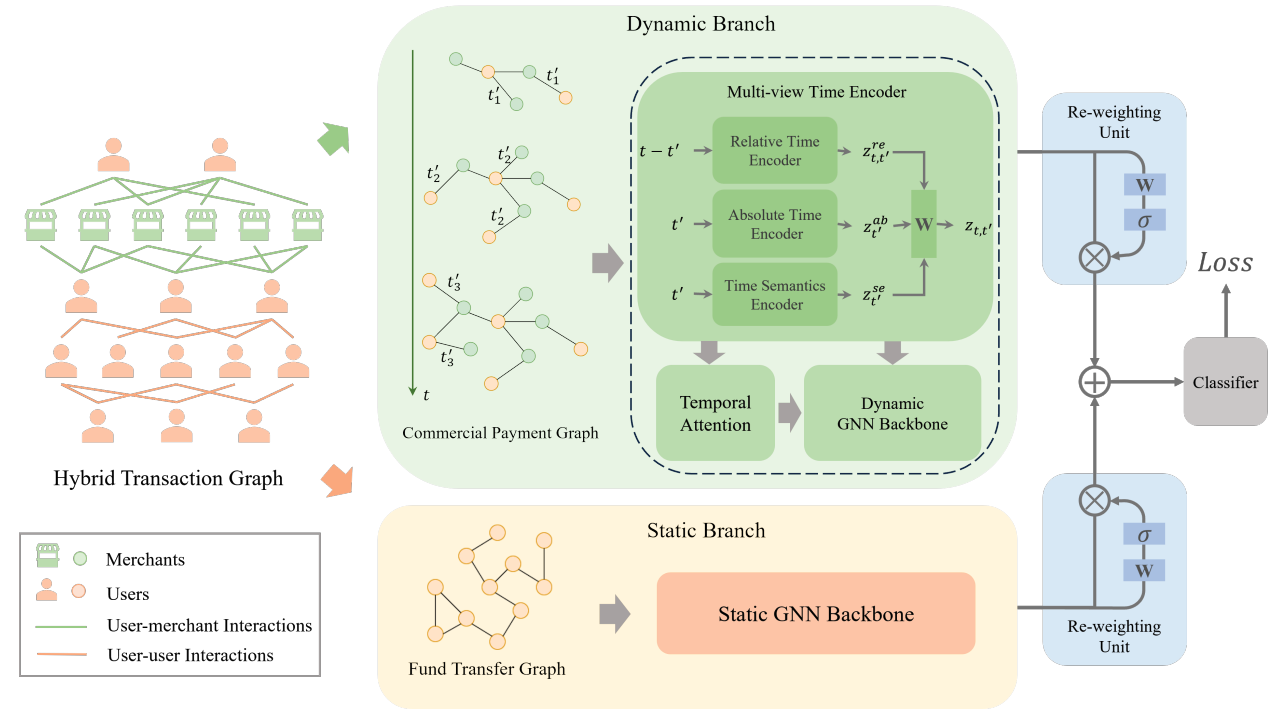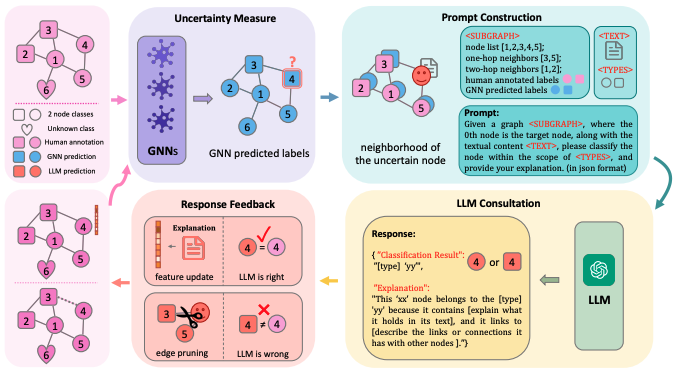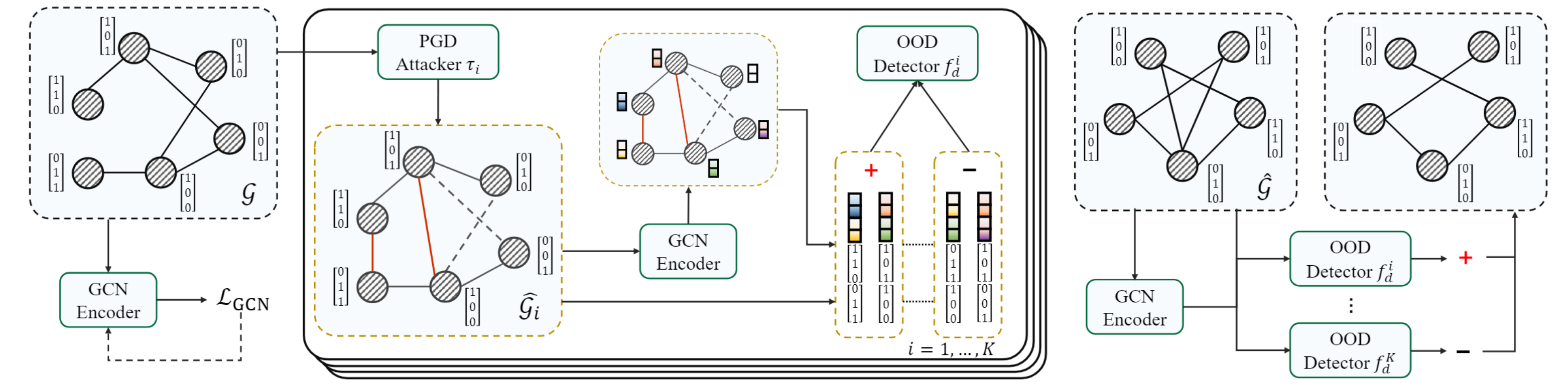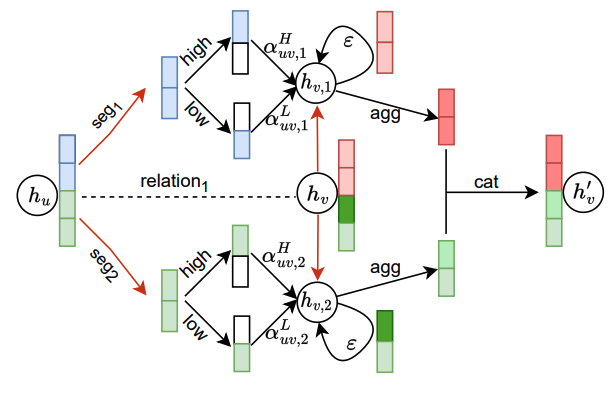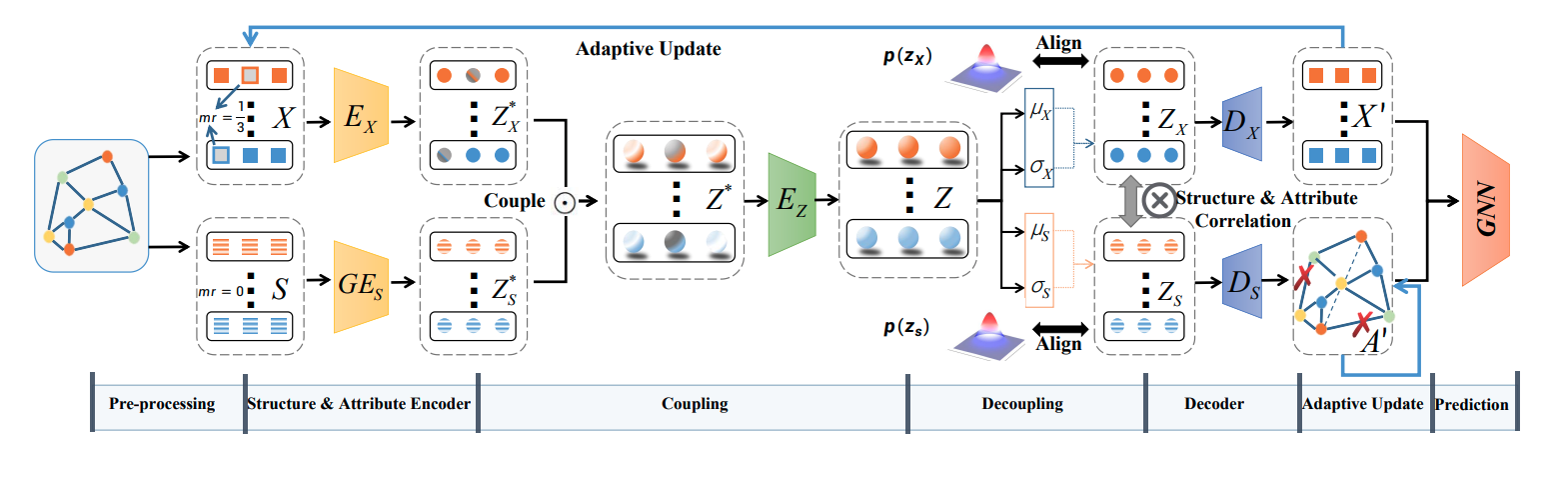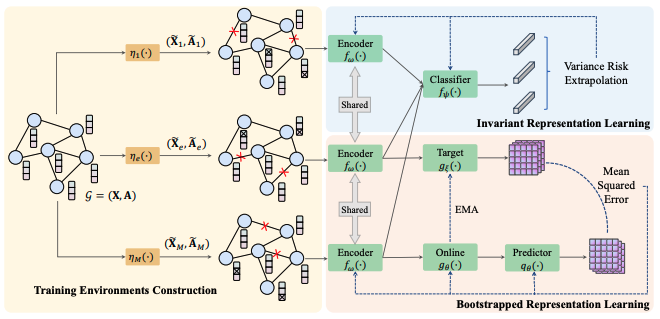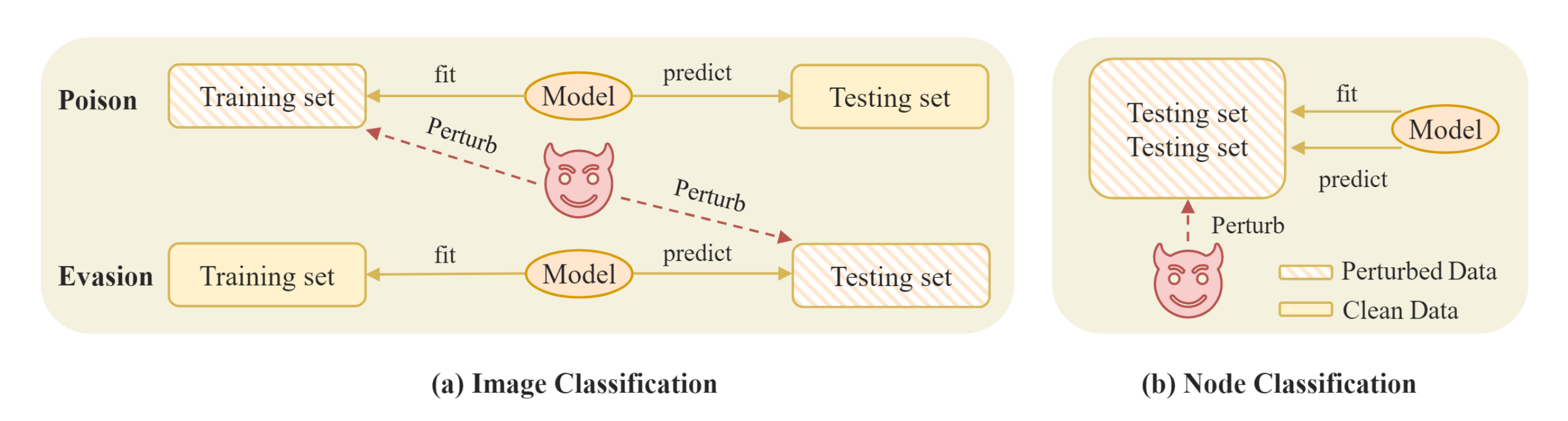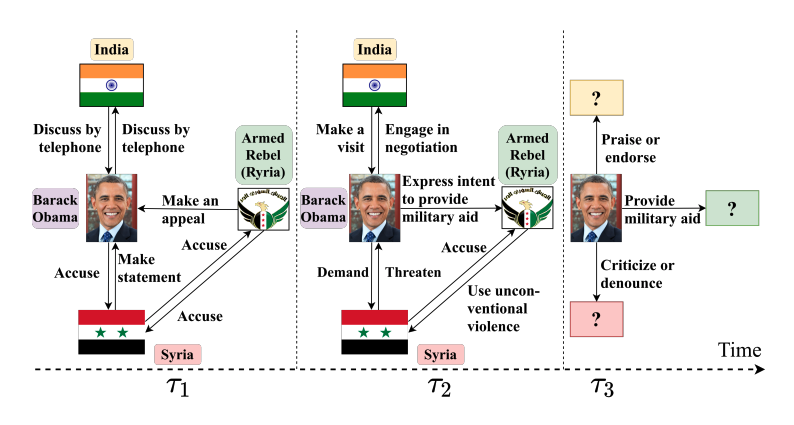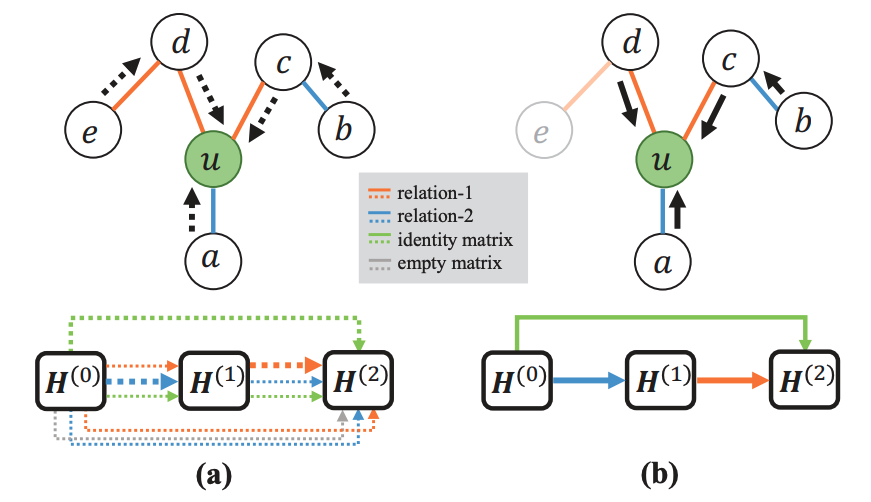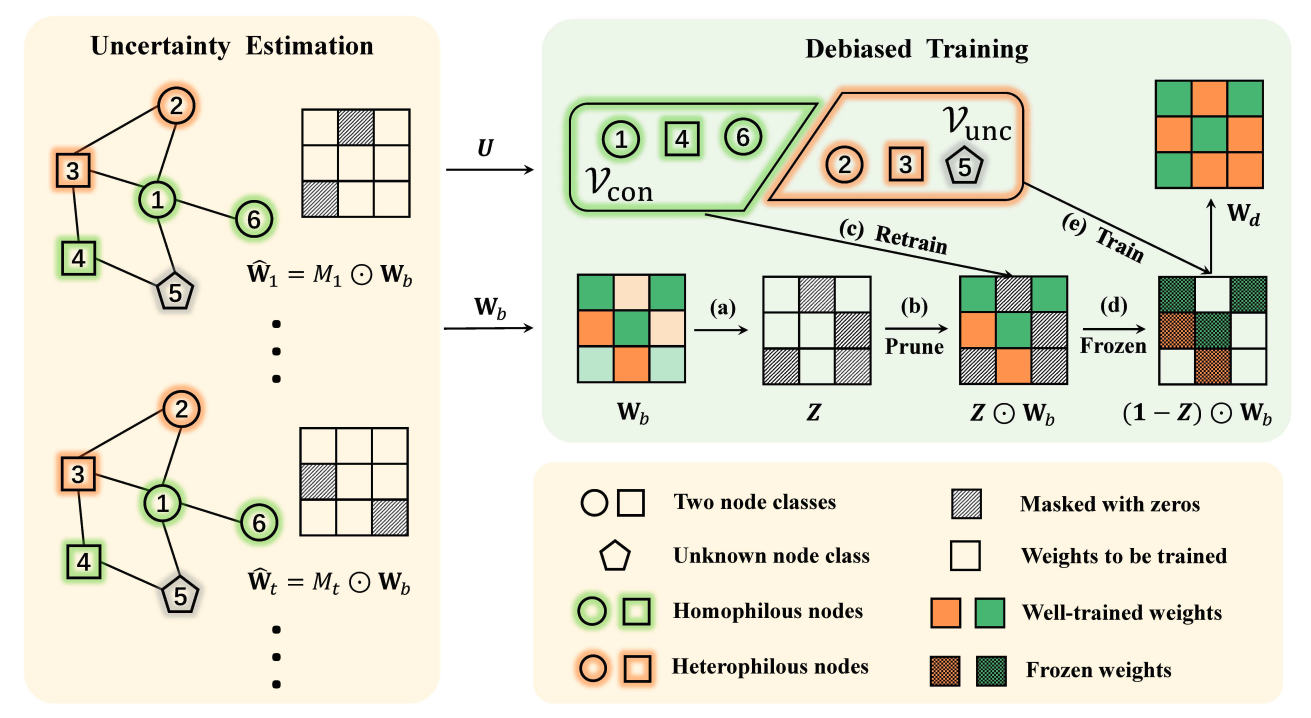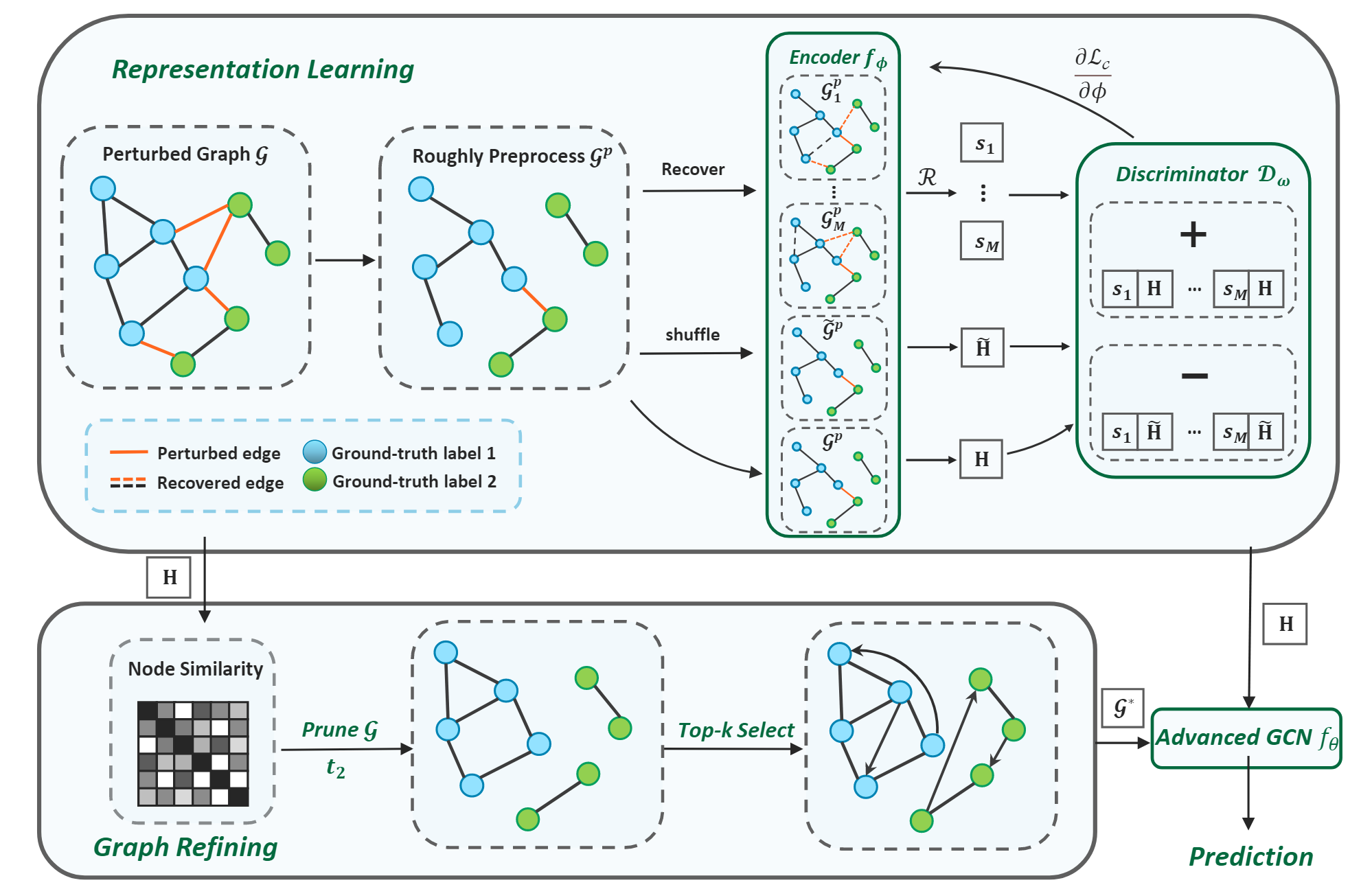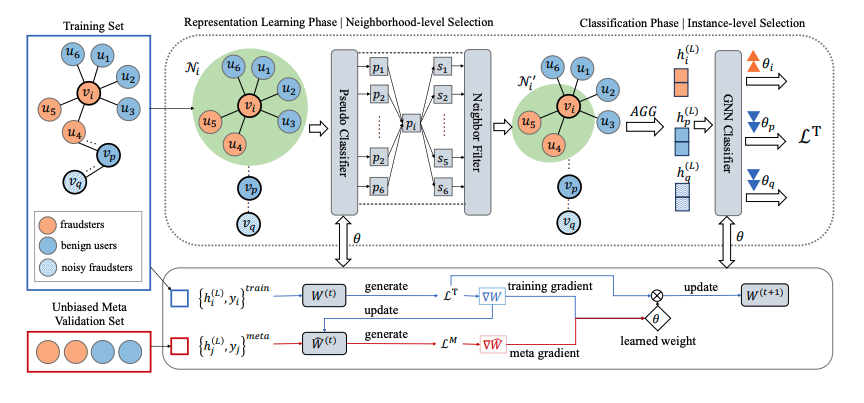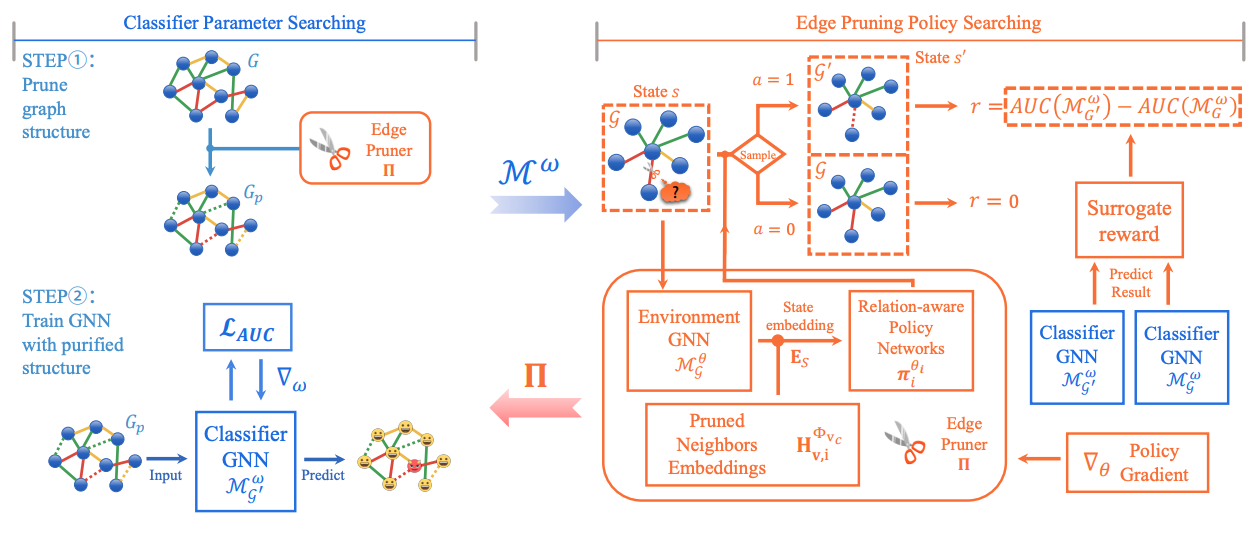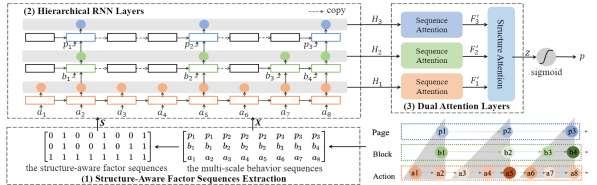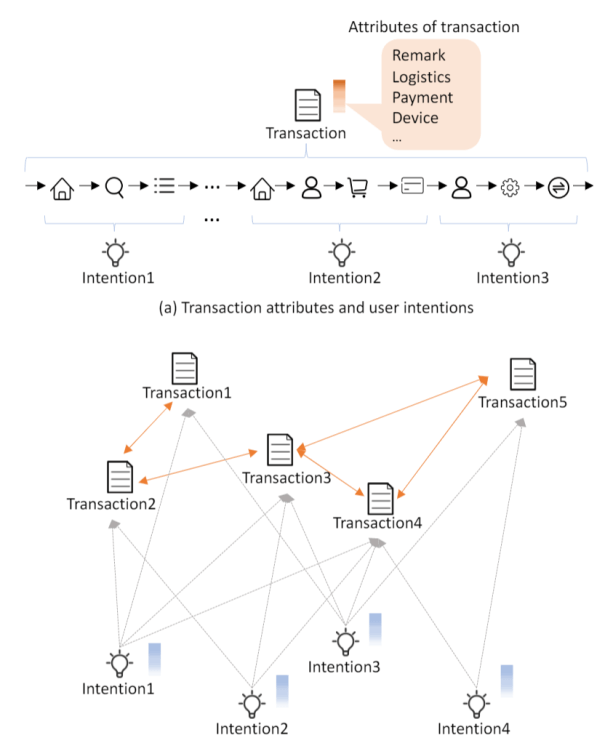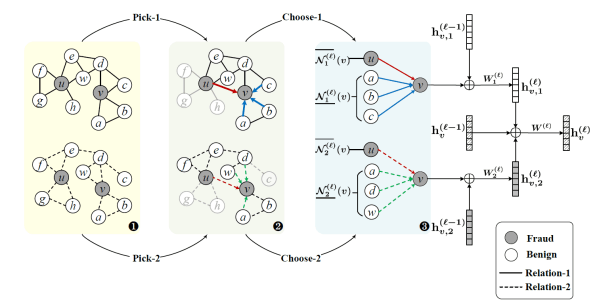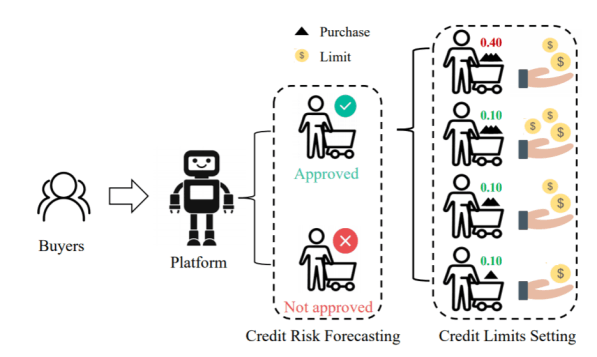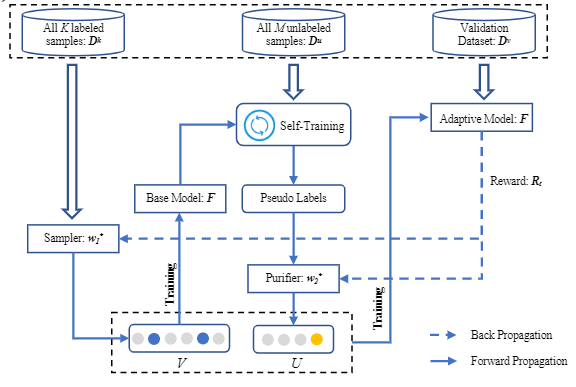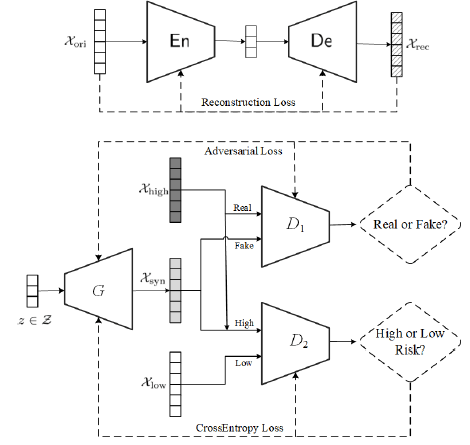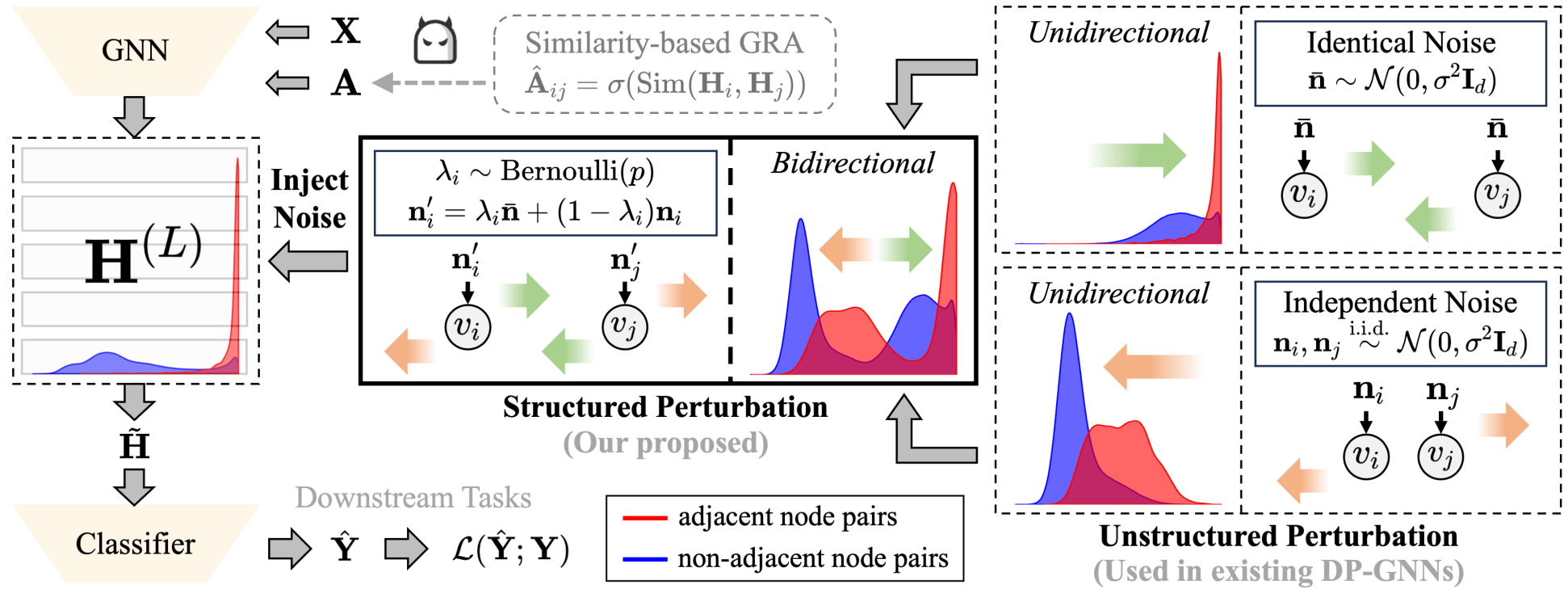
In this paper, we propose a novel Differentially Private Graph Neural Network based on Structured Perturbation (GRASP), which combines independent and identical noise to achieve bidirectional shifts in the embedding similarity distribution, thereby effectively disrupting the ranking structure and enhancing defense against Graph Reconstruction Attacks (GRA). [paper] [code]